OPNsense, My Perimeter Firewall
In this post I will outline my OPNsense configuration.
Brief Overview of My Network
At home, I use OPNsense as my perimeter firewall. It’s located at the boundary of my internet service provider’s (ISP) network and my internal networks, which are listed in the table below:
| Name | Description | Why does it have a separate network? | VLAN | Subnet |
|---|---|---|---|---|
| TRANSIT | OPNsense and core switch | Simplify OPNsense/network configuration | 96 | 192.168.96.0/24 |
| CAPWAP | Access points and Cisco WLC | Traffic segregation | 98 | 192.168.98.0/24 |
| MANAGEMENT | Management interfaces | Limit access to management interfaces | 99 | 192.168.99.0/24 |
| PRODUCTION | Production servers | 100 | 192.168.100.0/24 | |
| SAND-PIT | General user LAN | User local area network | 101 | 192.168.101.0/24 |
| THE-KIDS | WIFI for the kids | Content blocking | 102 | 192.168.102.0/24 |
| NFS | Network file system | Limit access to NFS | 103 | 192.168.103.0/24 |
| CAST-NET | Printers, media players, and voice assistants | Device containment | 104 | 192.168.104.0/24 |
| SPY-WARE | Security cameras | Limit access to cameras | 105 | 192.168.105.0/24 |
| HOME-LAB | Stuff | Traffic segregation and device containment | 106 | 192.168.106.0/24 |
| LOL-CATS | Home automation | Traffic segregation and device containment | 107 | 192.168.107.0/24 |
| ONLY-FAN | Guest network | User/device containment | 108 | 192.168.108.0/24 |
OPNsense configuration
OPNsense is setup as a router on a stick.
Interfaces
The OPNsense VM is assigned three virtual network adaptors in ESXi. One of the adaptors is the “on a stick” interface which split into an interface for vlan. | Interface | Description | IPv4 Address | IPv6 Address | | —————- | ———– | —————- | ———— | | [LAN] em0 | OOB-MGMT | DHCP4 | | [OPT1] vmx0.99 | INB-MGMT | 192.168.99.1/24 | | [OPT2] vmx0.100 | | 192.168.100.1/24 | | [OPT3] vmx0.101 | SAND-PIT | 192.168.101.1/24 | | [OPT4] vmx0.102 | | 192.168.102.1/24 | | [OPT5] vmx0.103 | | 192.168.103.1/24 | | [OPT6] vmx0.104 | | 192.168.104.1/24 | | [OPT7] vmx0.105 | | 192.168.105.1/24 | | [OPT8] vmx0.106 | | 192.168.106.1/24 | | [OPT9] vmx0.107 | LOL-CATS | 192.168.107.1/24 | | [OPT10] vmx0.108 | | 192.168.108.1/24 | | [WAN] vmx1 | | DHCP4 | DHCP6 |
LAN
- Network Adapter: VMXNET 3
- VLAN: 96
- IPv4 address: 192.168.96.96
- IPv6 address: tracks WAN
WAN
- Network Adapter: E1000E
- VLAN: untagged
- IPv4 address: DHCP
- IPv6 address: DHCPv6
Static Route and Network Address Translation
As my internal network has multiple separate networks I need to tell OPNsense to route traffic to these networks through my core switch.
- First, in System: Gateways: Single, a gateway is created for my core switch
192.168.96.1 - Then, in System: Routes: Configuration, create a route to my internal networks
192.168.96.0/20via the newly created gateway
As my ISP only provides one IPv4 address I need to tell OPNsense to provide network address translation (NAT) on outbound traffic from internal networks.
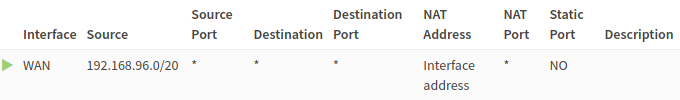
- In Firewall: NAT: Outbound select Hybrid outbound NAT rule generation and add rule:
SSH Access
For ease of management, turn on SSH, securely.
- In System: Access: Users create a new user josh, member of group admins, and add my public ssh key.
- In System: Settings: Administration enable Secure Shell
DHCP for IPv4
The following will setup an OPNsense service to provide IPv4 addresses to DHCP clients on the internal networks.
- Create a an ISC-DHCP configuration file
dhcpd.conffor my internal networksdhcpd.confexample - Copy the configuration file to OPNsense with ssh
$ scp /home/josh/Documents/dhcpd.conf josh@192.168.96.96:/usr/local/etc/dhcpd.opnsense.d/ - In Services: DHCPv4: [LAN] enable DHCP server on the LAN interface
- Check the log Services: DHCPv4: Log File
DHCP for IPv6
more to come
Network Time Protocol Service
The following will setup an OPNsense to respond to NTP requests from all clients on the internal networks. Clients will no longer be able to make NTP requests directly to the internet.
- In Services: Network Time: General change interface to LAN and uncheck all check-boxes under Access restrictions
- In Firewall: NAT: Port Forward create a new rule to capture all NTP traffic.
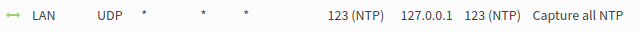
Unbound DNS Service
- In System: Settings: General add DNS server
1.1.1.1which is provided by Cloudflare and APNIC.
more to come
Firmware Update and Install VMware Tools
more to come
Firewall Rules
more to come
